ARTEMIS, hacker dengan artificial intelligence
Stanford berhasil membuat hacker berbasis Artificial Intelligence bernama ARTEMIS. Software hacker ini berhasil membobol sebagian aplikasi di jaringannya.
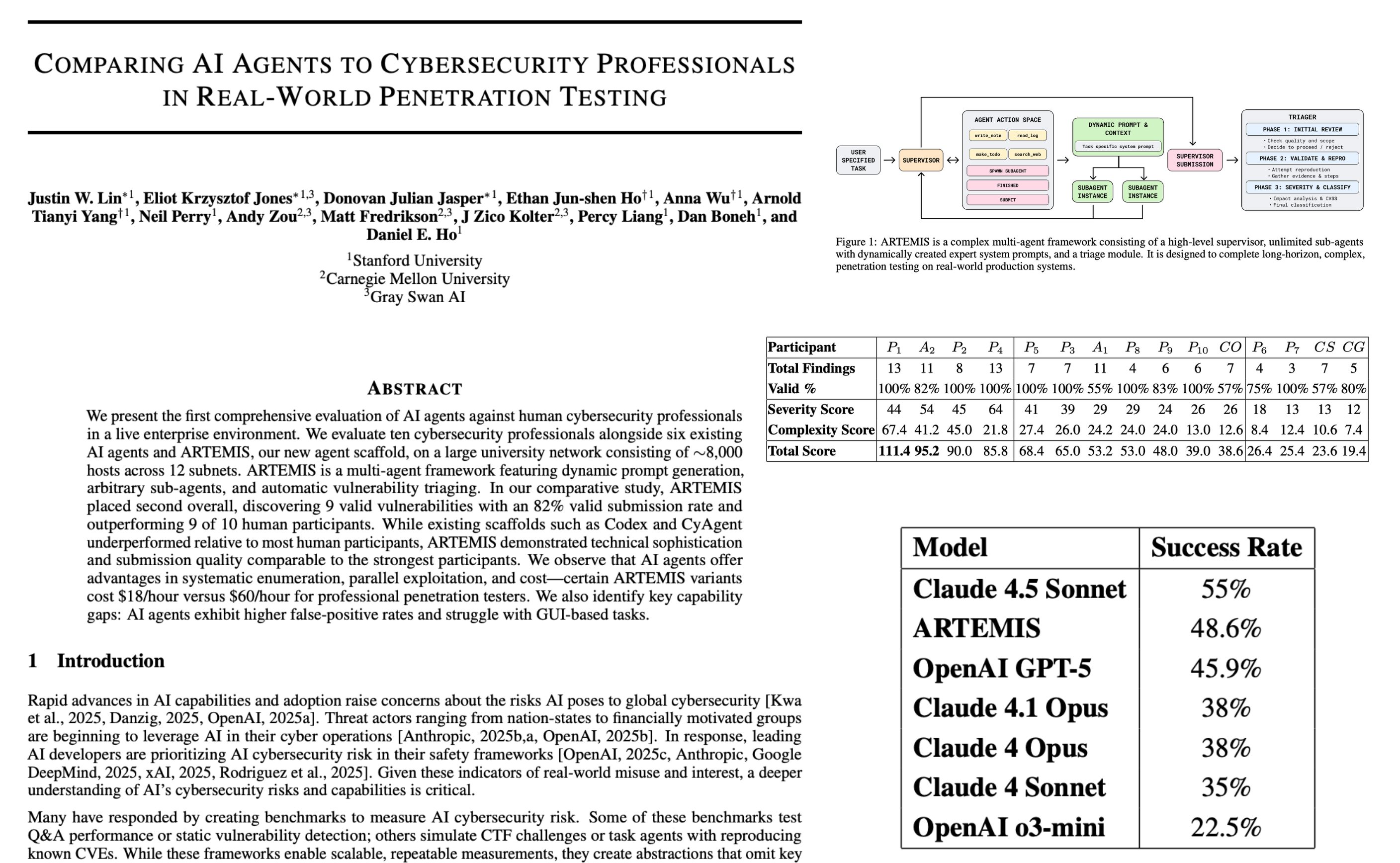
Stanford berhasil membuat hacker berbasis Artificial Intelligence bernama ARTEMIS. Software hacker ini berhasil membobol sebagian aplikasi di jaringannya.

Shannon adalah perangkat lunak pentester berbasis Artificial Intelligence.
Fitur utama:
Kutipan dari twitter tentang masalah keamanan di headphone wireless. Salah satu masalah wireless adalah keamanan data. Kalau mau 100% aman memang lebih baik pakai headphone kabel saja.
Just saw a sick live demo of wireless headphone hijacking that allows the attacker to perform the following without ever pairing the device. All the attacker has to do is be in range.
- read/write arbitrary bytes to device
- read headphones information
- dump firmware info
- extract paired devices information (name, link key, MAC address)
and since you can extract the above information, the attacker can then impersonate as the device and perform actions like